Cybersecurity research from a business and economic perspective
The Chair of Innovation and Risk Management is involved in the research of the KASTEL Security Research Labs (SRL) at the Karlsruhe Institute of Technology (KIT). As part of the KASTEL Institute for Information Security and Reliability, the chair makes a research contribution to the economics of cyber risk management with a focus on game theory and business process analysis for production systems, behavioural economic approaches to human factors & usability and quantification of cyber risks from a predominantly business and economic perspective.
A - Economic Cost Estimation & Optimal Allocation of Cybersecurity Resources
Investing in cybersecurity should be both effective and efficient. This presents organisations with non-trivial problems for several reasons
The mapping problem
Many types of risks (e.g. data breaches) cannot be directly mapped to specific business processes, which is a prerequisite for assessing the impact. Our approach is to apply process value analysis (PWA) as an established method for determining the value of disrupted processes, either at an industry or supply chain level (Kaiser et al. 2021a).
The prioritisation problem
The prioritisation of system elements and potentially affected business processes is difficult, which is mainly due to the networking of the systems.
The scaling problem
Even if you have decided which defence measures to focus on as a priority, these often need to be scalable in practice. Scalability gives organisations additional flexibility. In the security solutions market, 'off-the-shelf' products are not necessarily suitable for all organisations and need to be tailored to specific needs. For SMEs, this option is what makes some security solutions affordable.
We approach the prioritisation and scalability problem by combining game-theoretic analysis, Cyber Threat Intelligence (CTI, Kaiser et al. 2023) and a Countermeasure Selection & Allocation (CSA) approach. The CSA approach was developed for industrial control systems (ICS), with the KASTEL Production Lab PoC demonstrator from Fraunhofer IOSB serving as the use case.
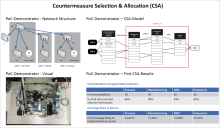
Figure 1: Countermeasure selection and allocation
The assessment problem
In order to arrive at a coherent risk assessment, it is difficult to estimate the expected damage. Attack probabilities result from a highly dynamic attack landscape and the vulnerabilities of the system; the consequences of cyber attacks include material and immaterial, direct and indirect, monetary and non-monetary costs.
We use Cyber Threat Intelligence (CTI) to monitor and simulate attack frequencies and targets. To improve cost estimation, we transfer our research from the areas of supply chain risk management and humanitarian logistics to the area of cyber risk management (Diehlmann et al. 2021; Kaiser et al. 2021b).

Figure 2: Cyber Threat Intelligence (CTI)
[Researchers involved: Dr Christian Haas, Dr Ankush Meshram, Jonas Vogl, PD Dr Ingmar Baumgart, Prof Dr Marcus Wiens, Prof Dr Jürgen Beyerer]
B - Game Theoretical Analysis of Security & Privacy
Interactive assistance is playing an increasingly important role in many modern production processes. As these systems collect and process information about human workers in order to support them in their tasks, the privacy-compliant and secure design of assistance systems is an important concern. With Fraunhofer IOSB's Production Lab 4Crypt demonstrator, we develop and analyse interactive assistance systems that are both transparent (in the sense of being comprehensible for their users, but also in terms of the operators' data protection obligations) and trustworthy (in the sense of being data protection-compliant and comprehensibly secure).
In the use case under consideration, the game-theoretical analysis shows that an employer has a systematic incentive to submit unlawful requests to view the video recordings, which can lead to discrimination, increased stress and reduced trust among employees. This emphasises the particular relevance of the cryptographic solution. If assistance systems are viewed through the lens of signalling games, it should not be possible to draw conclusions about the individual employee in the event of a failed approval (counterproductive signal). From a game theory perspective, the system is only information-proof if an independently acting works council is responsible for granting consent. In companies without a works council (< 5 employees), this role could be assumed by an elected shop steward, although the signalling effect cannot be avoided.
The level of trust among employees is of great importance for the working atmosphere and labour productivity. The analysis confirms that the two most important sources of trust are (I) the integrity of the encryption components and (II) the independence and consensus principle of information sharing. These requirements are generally not met by established video assistance systems, meaning that 4Crypt makes an important contribution to increasing security and privacy in the workplace.
[Researchers involved: Dr Pascal Birnstill, Dr Paul Wagner, Dr Jeremias Mechler, Prof. Dr Marcus Wiens, Prof. Dr Jörn Müller-Quade, Prof. Dr Jürgen Beyerer]
C - Behavioural economics research on user behaviour in the context of cybersecurity (esp. "human factor" and user risk behaviour)
Optimal decisions in the field of cybersecurity involve decisions under risk and uncertainty in complex, networked environments. Attackers exploit this complexity by exploiting human vulnerabilities through e.g. social engineering tactics. One focus of our work is the threat posed by phishing emails, in particular the risk behaviour of users under stress. While previous research has primarily focussed on user characteristics and source credibility, little attention has been paid to contextual factors that influence information processing, such as time pressure. We are interested here in the impact of stress factors on risk awareness, the consequences for labour productivity and the effect of no-phish training videos from the KIT research group SECUSO.
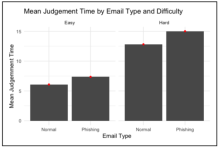
Figure 3: Mean Judgement Time by Email Type and Difficulty
References
Kaiser, F. K.; Dardik, U.; Elitzur, A.; Zilberman, P.; Daniel, N.; Wiens, M.; Schultmann, F.; Elovici, Y. & Puzis, R. (2023). Attack Hypotheses Generation Based on Threat Intelligence Knowledge Graphs. IEEE transactions on dependable and secure computing, 1-17. doi:10.1109/TDSC.2022.3233703
Kaiser, F. K.; Wiens, M. & Schultmann, F. (2021a). Use of digital healthcare solutions for care delivery during a pandemic - chances and (cyber) risks referring to the example of the COVID-19 pandemic. Health and Technology. doi:10.1007/s12553-021-00541-x.
Kaiser, F., Wiens, M., & Schultmann, F. (2021b). Motivation-based Attacker Modelling for Cyber Risk Management: A Quantitative Content Analysis and a Natural Experiment. Journal of Information Security and Cybercrimes Research, 4(2), 132-147.
Rajabzadeh, H. & Wiens, M. (2024). Resilient and sustainable energy supply chains: insights on sourcing and pricing strategies in a non-collaborative and collaborative environment. International Journal of Production Research, 1-32. Doi: 10.1080/00207543.2024.2331556
Shirafkan, N.; Wiens, M.; Rajabzadeh, H. & Shaya, N. (2024): Synergising Multi-Layer Blockchain Technologies for Enhanced Security and Operational Efficiency. Proceedings of the 11th Annual Conference of the Operations Research Society of Germany (OR 2024), Munich, Germany, 3-6 September 2024.